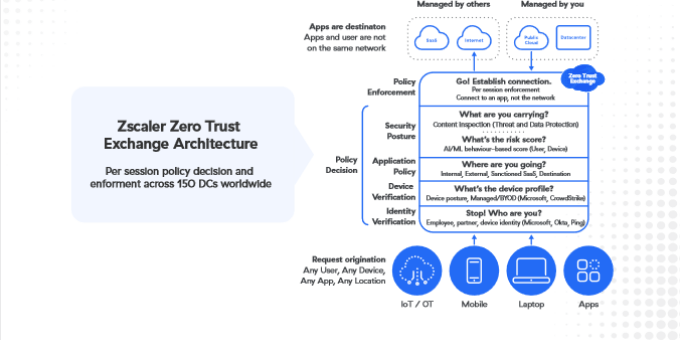
Many in IT security believe zero trust is a game changer, a fundamental rethink about enterprise
security and protection of the networks and resources that house our best ideas, connect our brightest talent, and grant access to transformative productivity tools.
But to understand how truly revolutionary the zero trust model is in cybersecurity, it’s necessary to
understand the weaknesses of the legacy network security approach and how the idea of zero trust
architecture evolved into one that fundamentally overhauls decades-old thinking.
Hub-and-spoke and castle-and-moat are the two primary metaphors used to describe legacy
network architecture and network security, respectively. Fittingly, the imagery used in both
has been around for a while.
Hub-and-spoke network architecture refers to satellite networks arranged around a central hub.
This model entails routing internal and external traffic back through a security stack at a primary
data center before it proceeds to its destination. While this approach worked for a while, it’s
become more complicated and expensive given cloud adoption, distributed workforces, and the
increasing importance of mobility in business.
This article is posted at zscaler.com

Please fill out the form to access the content








